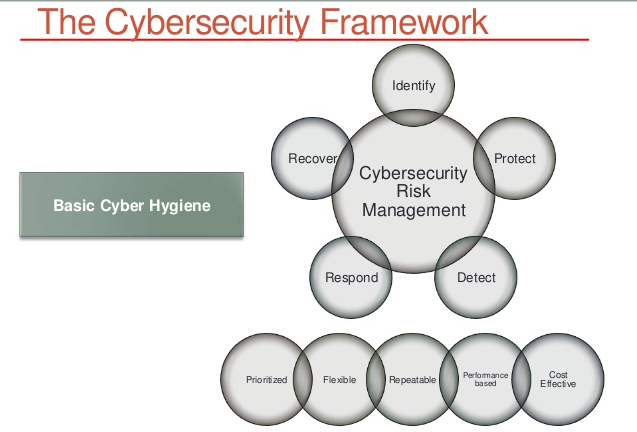
Effective risk management is a core component of governance and must be embedded within the organisation. A framework is needed to effectively identify, analyse, evaluate, and manage cyber security risks. The framework supports consistent decision-making and prioritisation within an organisation, maximising the benefit of investment in cyber security.
Tri-Paragon’s cybersecurity risk consulting services will help identify and evaluate the risks and vulnerabilities your company may be facing now. Using our risk consulting services will allow your personnel to focus their time and attention on growing the business and serving your customers. Our risk consulting services are practical and affordable. We perform remote cybersecurity risk assessments for your organization.
Tri-Paragon uses a state-of-the-art security and risk assessment platform that can be utilized for facility compliance and security risk assessments. It helps to reduce exposure to liability, manages risk, monitors, and maintains security, and tracks continuous improvement.
Cybersecurity Best Practices
Your organization’s goal should be to strive for the capability to prevent, detect, and respond to cyber attacks targeting your data center. Malware, spyware, and hacking are all examples of cyber threats to data centers. Cybercriminal activity is expected to be one of the largest challenges’ humanity faces in the next two decades and data centers are always going to be in the crosshairs. Fortunately, there are steps you can take to minimize risks.
Keep Servers and Systems Updated
The first and easiest step to protect your data center is to always keep servers and systems updated. While applying updates and patches is not always convenient, it is important to do so as soon as possible. These often get pushed aside because “things are running just fine” yet this is what cyber criminals are hoping you will do. When an organization releases updates or patches for their product, it is often because they are fixing a security gap that was identified.
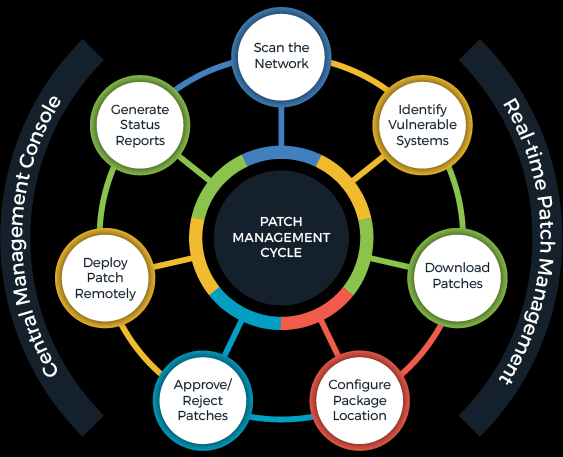
Imagine you just bought a car and after a week, the back window stops closing. If the manufacturer offers to fix the window for you, would you say, “maybe later”? Until you fix the window, there remains an easy way for someone to break into your vehicle. Keeping your systems and server updated is an easy way to remedy vulnerabilities before they can be exploited.
Encrypt Your Data
Any data at rest or in motion should be encrypted. This translates your data into another form that can only be deciphered with the correct code, ensuring your data is not easily visible to anyone that should not have it. If your organization permits portable storage devices, ensure these are encrypted so when lost or stolen, the data will remain safe. Use network-level encryption to secure your data when it travels between endpoints and use server-level encryption to protect your data when it is at rest.

Automated Network Analysis
Defending your network and scanning for threats should be a top priority and should happen 24/7. This is because most cyber attacks are over the network, so having a good front line defense will prevent the spread of malware and any data breaches. Anomaly detection, keyword matching, data monitoring, and other methods will alert you to any suspicious communications that have gotten past your firewall. Consider implementing Tri-Paragon’s AgileBlue Security Operations Center as a Service built on Machine Learning + User Behavior Analytics to provide 24×7 monitoring, detection and prevention from modern cyber threats.
Antivirus
Antivirus programs are historically signature-based. As malware is discovered, file names and indicators of compromise are cataloged in antivirus engines. As each file enters a network or computer, it is scanned against the signature list and quarantined or deleted when there’s a match. This is a security issue because, in a report by SentinelOne, “only 50% had been previously submitted to malware repositories. And of that half submitted, only 20% had corresponding signatures from existing anti-virus engines.”

Antivirus systems operating with AI focus on detecting unusual behavior by programs rather than matching signatures. This is typically more efficient because most malware is designed to function differently than is the standard operation of the computer system, and they can be detected from these actions. This allows these AI-based antivirus systems to detect zero-day exploits and other previously unseen/cataloged malware. Another good reason to consider Tri-Paragon’s AgileBlue SOCaaS.
Monitor and Restrict Access
One of the most effective methods of preventing cybersecurity incidents is to Implement and enforce access restrictions. This applies to both physical and cyber efforts. Limiting access to users will reduce unnecessary risk and limit the chance of a breach. According to Verizon’s 2020 Data Breach Investigations Report, https://enterprise.verizon.com/resources/reports/dbir/ 30% of breaches were caused by insiders. This includes falling for phishing attacks, intentional malice, or losing credentials. Limiting a user’s access to documents and data that they do not need will help reduce the impact of an incident they cause. Start by reviewing permissions for every user that has access to your network.
Implement a Zero Trust Architecture
Zero Trust architecture has become known in cybersecurity as the act of eliminating the notion of trust from an organization’s network. The idea behind this is that to protect modern digital environments, you must never assume that all users act responsibly and follow policy on a regular basis, or that those users have not been compromised. Once on the network, users can copy or transfer any data they have access to, making them a large vulnerability. With the assumption that threats can and do come from inside an organization, more focus is then placed on securing data and segmenting access.
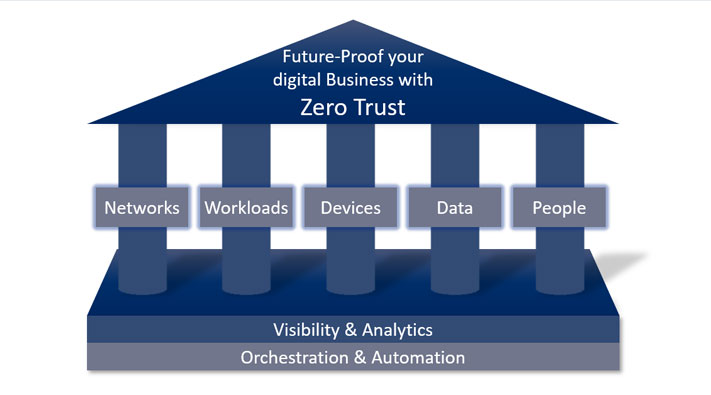
One good practice is to create secure zones in your network, which will help layer security. These zones should include a test area, a development zone, and a production zone. Prior to any new code or applications being executed, its recommended to scan them for vulnerabilities that can be exploited.
Implement Cybersecurity Policy and Training
It is often said that humans are both the strongest and weakest components of security. To reduce data center vulnerability, provide security awareness training and set policies that enforce proper security behavior. Creating rules and policies does not help if employees are not aware of them and understand them. Employees need to know how data breaches occur and how their actions impact security.

To assist with personnel training, Tri-Paragon's 'AutoEnrol' feature enables you to rapidly deploy training programs unique to your employees' security weaknesses, with continuous management made easy through automated course invites, reminders, and weekly summary reports.
Tri-Paragon recommends the following approach to managing the cybersecurity risk in your organization:
Initiate a Cybersecurity Risk Reduction Program
- Conduct a cyber security risk assessment using Tri-Paragon’s state-of-the-art security and risk assessment platform. Prioritize actions based on the results of the assessment focusing on highest risk areas first.
- Install Tri-Paragon’s SOCaaService. Advanced Technology & Threat Intelligence Network protects your network, cloud and endpoints including vulnerability management, monitoring, and analysis. We extend your security operations to bridge people, processes, and technology for 24×7 support. Tri-Paragon’s SOC-as-a-Service Platform is built to learn your normal network and human behavior then develop algorithms to understand when signs of a malicious intent are identified. Our platform analyzes network traffic and security data and autonomously identifies, assesses, and processes cyber threats. 24X7 our platform is monitoring and securing your:
- Cloud, on-prem network and IoT applications
- All devices and users
- SaaS based applications
- Implement Tri-Paragon’s cybersecurity training program for all of your personnel
- Review and adjust as necessary your Patch Management processes and resolve any gaps identified.
- Encrypt your data
- Reassess and adjust your access control policy and implement changes required.
- Implement a Zero Trust Architecture.
Tri-Paragon’s Senior Consultants are here to assist in organizing, planning and managing your program to achieve the desired results within your budget and resource limitations.

For additional information on Tri-Paragon’s:
- Cybersecurity Risk Assessment Tools
- Security Operations Centre as a Service
- Intelligent Training Platform
- Program Management
call Roy at 1 (416) 865-3392 or
email us at info@triparagon.com .
https://www.triparagon.com/
See how Tri-Paragon’s AgileBlue Machine Learning + User Behavior Analytics SOC-as-a-Service can help reduce the risk of a breach. https://agileblue.com/